Mobile health technology and healthcare apps are becoming more important for the healthcare industry. Users actively install a mobile medical app on their devices to count the number of steps done during the day, measure heart rate, or consult a physician.
With only 4.8 percent of the world’s population having no health problems, and with 2 billion smartphone users in the world, it is high time for healthcare software companies to bring a revolution of change with secured healthcare app. As the Electronic Health Reporter says:
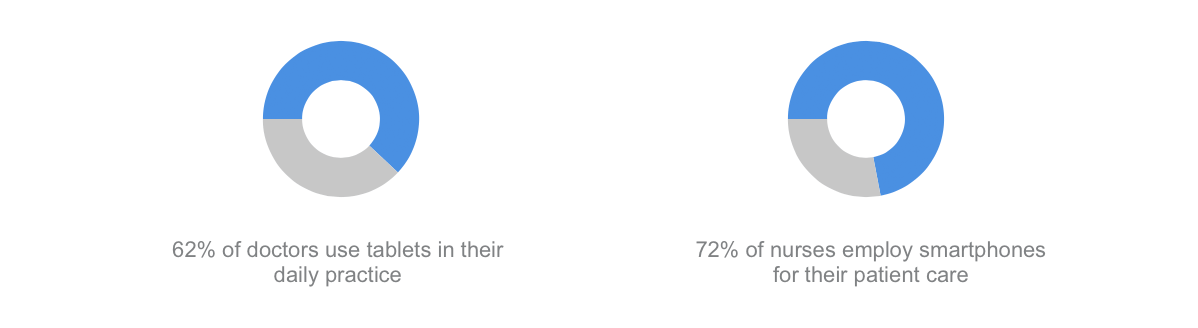 So it’s vitally important to protect the personal data.
So it’s vitally important to protect the personal data.
Health industry companies are taking a step ahead to meet the needs of customers by evolving themselves as healthcare software companies and coming up with secure mobile medical app development.
But as soon as a healthcare app is downloaded, it has to fulfill a number of conditions for the customer to be assured of the service. But is it possible for healthcare software companies to build a secure mobile medical app? Let’s have a deeper look into the problems and their solutions.
Table of Contents
Does your mobile app need to be HIPAA compliant?
Good question. What if your app is related to a health-care sector? Perhaps, it briefly touches the topic, and you could get away with non-compliance. Here’s the list of questions to answer to understand if your app needs it, given you are interested in marketing to the US healthcare market.
Who is using the app?
Is a doctor or a healthcare provider involved? If your app facilitates interaction between the doctor and the patient, then it most definitely falls under HIPAA compliance. If your app is created for the user alone, there is a good chance it doesn’t require to be HIPAA compliant, unless it matches the patient with his health data. Let’s say the app is a fitness tracker that tracks heart rate variability. Since it involves no interaction with the hospital, the regulations do not apply here.
What type of data about the user does the app manage?
If personal data is connected with medical data (names, medical record number, SSN, etc.), it qualifies as Protected Health Information. If any medical data is managed by the app, like the course of diagnosis or actual treatment and prescriptions, the app absolutely must be HIPAA compliant. If the user enters information on his own (e.g. reminder to take pills), then the app need not be HIPAA compliant. Discover the power of Generative AI Use Cases in Healthcare industry.
Answering these 2 questions will help you understand if your app must comply with HIPAA security technical safeguards in the US market.
How to Build a Secure Mobile Medical App According to HIPAA?
In order to build a protection of PHI and data secured app, one should keep the following things in mind and avoid all the possible shortcomings in the app:
-
You need to know the rules and regulations of the audience and field you are targeting so that you meet all the laws of the law governing bodies. Every section of the healthcare industry has its own legal act, and you should be completely up to date about all of them.
-
The U.S. Department of Health & Human Services’ (HHS) Office of Civil Rights (OCR) oversees compliance with HIPAA (Health Insurance Portability and Accountability Act) privacy requirements. In order to avoid any obstacles in future, healthcare software companies should be in sync with all the regulations of HIPAA to be sure that the possibility of data leakage and unauthorized access are reduced to zero.
-
Again when it comes to regulations the complexity of the rules depends on the footprint you plan to have for your app. If it plans to save data then privacy and security laws are quite strict. In general, US law governing PHI applies to data collected in the course of providing and paying for healthcare. Privacy and Security regulations govern how the collected data is being used and protected. You can also hire some attorney to explain these terms better to you when you are building a healthcare app.
-
Healthcare software companies are very sensitive in such cases and no mistake is allowed. In fact, even a single case can put the organization in danger. Therefore one should find more of such guidelines when testing an app so that before release everything is secured and researchers and developers can be assured.
-
Following all the guidelines is really important, but keep in mind one more valued aspect – an opportunity to get insights for your app. To stand out healthcare software companies have to get all inputs initially to have maximum downloads of their app and excel among other apps.
-
If your healthcare related communication channel and data on a device are critical, protected or can provide the access, they must be encrypted to make users’ personal information safe when they download the app. Healthcare software companies cannot miss taking this step to build trust with their customers.
-
It is recommended to review the HIPAA compliance checklist to ensure that your organization complies with the HIPAA privacy regulations covering the security and privacy of confidential patient data.
Technical part of HIPAA compliance
To pass HIPAA Compliance audit, your system should secure Protected Health Information being processed\exposed. Here are general technical recommendations.
- Prevent any unauthorized access. Access to the application should be restricted after some time of user inactivity by automatically signing out or locking the session with pin screen or automatic logout, for instance.
- Avoid storing or caching (including HTTP caching) any sensitive data on the device. If you must store sensitive data (including authorisation tokens, session data, etc.), it should be strongly encrypted. Do not store any passwords.
- Interactions with the server should be performed via well encrypted SSL\TLS (Enable only strong ciphers (128-bit and up) and TLSv1). Certificates should be signed by a trusted CA for browser access. Restrict any non-encrypted access.
- Do not expose actual account numbers on the client side – use tokens instead.
- If you need to store sensitive data on the device, it should be custom encrypted in addition to standard device encryption APIs.
- Do not store sensitive data in RAM longer than needed.
- Tread with all client inputs as untrusted. Data should be validated and sanitised to prevent app crash, buffer overflows SQL Injections, and other attacks.
- Keep server configuration up-to-date; apply all software security patches fast.
- Disable verbose errors output on production.
- To prevent brute-force attacks, response to the client should be the same for both cases – if user does not exist or if username and password combination is invalid.
Why Should Healthcare Software Companies Follow All These Rules?
When any industry integrates IT module in their field, one cannot allow a breach of data. Similar is the case for healthcare software companies – they cannot surpass the rule of data security. HIPAA Compliance states the clear set of compliances all healthcare software companies should abide by. Once the healthcare software companies define the landscape of their audience after that they should understand the sensitivity of the audience to such cases. Any app which had stored PHI (protected health information) should follow the security guidelines before the app hits the market. The security of the customer’s information entails a financial responsibility and should be an ethical principle of healthcare software companies to maintain a good reputation in the industry.
Conclusion
A secured healthcare app development should always be the first aim of healthcare software companies.
As a software development company specialized in healthcare solutions, MOCG always makes sure that we follow HIPAA privacy rules and exclude any possibility of the law violation.
We’ll be happy to help you get it off the ground!